There has been so much political grist for the networks and the news world lately about hacked celebrity accounts that I wonder what sort of pretensions we are all operating under here. Wait. While we are at the beginning, I think I should rename this post from “The Future Will Be Hacked” to “The Future Was Hacked Already” or better yet, “You Already Lost All Your Junk, You Just Don’t Know It Yet.”
And what’s funny to me, is that there will be 5 of you that read this post. The other 200 can’t be bothered. And that is why All Your Base Already Are Belong To Us.

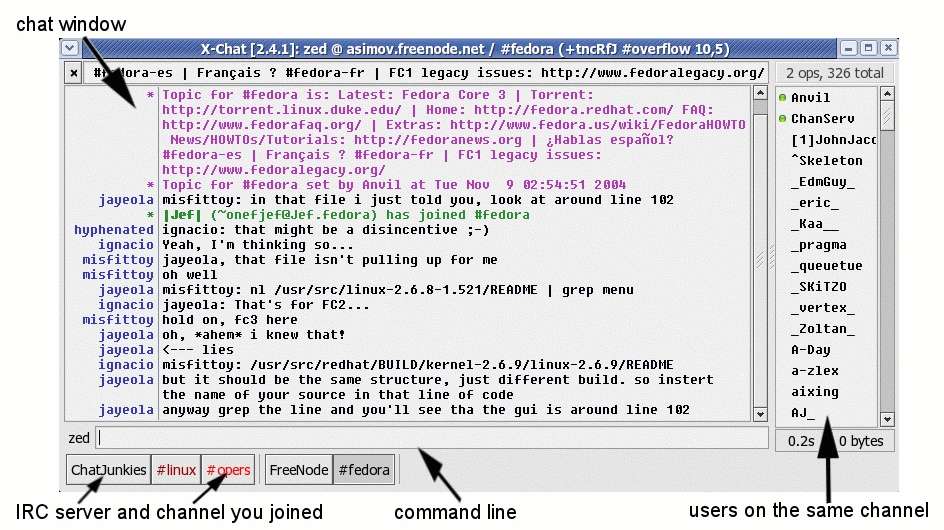
Let me just drop a little bit of Hacker Community insights on to you the random uninformed for a moment. This, this right here, is an IRC (Internet Relay Channel):
Looks really complicated. But its simply just a room with users all collecting and talking. Right? Think public group chat… on steroids. The column on the right are the people in the channel. The Command Line is where you can type your comment, or your room command. Going up the screen is the conversation back in time as you go up. Once you understand this little piece of technology we can begin to understand more about Anonymous, Hackers, etc. (This is so sadly remedial, I’m actually embarrassed to be explaining it out loud.) Regardless. That is a chat room.
But let me drop some heavier truths on you for a moment. See the names on the right? They probably aren’t all real users. Like _Zoltan_ as an example. He could be a human. Or he could be a bot that is built for a specific purpose or just general administration, or he could be a combination of the two. In a non-hacking chat channel a bot can be used for administering rights, securing the channel, kicking out people that swear, or abuse others… and they do it all automatically per the channel’s manifesto or rules. So let’s say I create a channel called #BakingCakes!! – and we are all about new recipes for Cakes. (Or what have you.) We could build the bot to capture every recipe someone dumps into the channel. And then you could query the bot to spit them back out to you by the name, or just export them to you, or whatever. Automation is powerful and can do many things… most of them good.
I remember writing a bot that would do a million things for my channel day and night. It maintained it while I was asleep and it made sure the channel was well admin’d. I once even wrote an encryption algorithm that allowed users to chat in open free text, it spit out garbled craziness to the channel and then the people that were privy to the script were then able to unencrypt what was said. Simple enough really. My bot was also my right hand man when things went sideways. I remember one particular day when someone tried to take over my channel because I’d amassed close to a hundred people in the channel and it was doing so well. They managed to hack access to an admin account that they used to kick me out of the channel. But I was then able to send remote controls into my bot in order to DOS (Denial of Service) attack the perpetrator off the internet and then I had my bot reestablish my credentials as the owner of the channel.
Bots are such an enormous part of the IRC world there have even been songs written about them. Boten Anna is a Swedish song telling the story of a female IRC user that was mistaken to be an IRC bot, but she was actually a real person. Months later, he learned that Anna was actually not a bot, but was his friend’s girlfriend; the embarrassment, he says, inspired him to create the song:
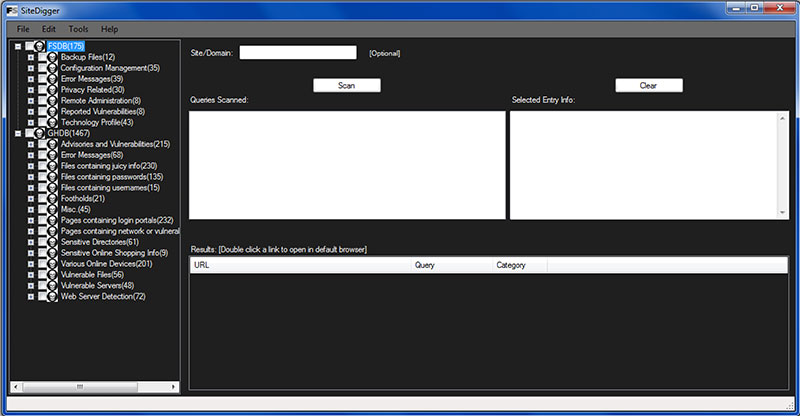
The fact that people mistake bots for humans and humans for bots is central to the culture and capabilities of IRC. It is from there that you can leap into the more nefarious world of Anonymous and hacking. If you can program a bot to capture recipes and fight IRC land wars for you… what else can you think to make it do? Hrm. Oh I don’t know, how about troll the internet for weakly protected websites? And when it finds one, why don’t you just call it out into the channel. Sure. Why not? Then people in the channel can go see how interesting the find is, open it up, turn it upside down and see what falls out. That is what the SecOps guys in Anonymous were doing regularly. Let’s be clear, you can do this right now. You don’t need an IRC Bot to do it for you. McCaffee has a free tool that will let you do this right now from your desktop:
So what is this? These are common known weaknesses that are already known. They are collected here and ready for you to ask away. I literally just installed this little app in 30 seconds. Once in, key in the site you want to know about. Maybe its your own wordpress website (which I did against this site the moment I opened it) or what have you… and just like that you begin to see attack vectors open up to you. Potential weaknesses and issues to use as leverage points. Once you know the server type, the type of the CMS, the patching and the versioning of everything it becomes very very easy to start create an attack strategy. But inside Anonymous the bots would spider the world perpetually day and night and cough out fascinating weaknesses. Lackeys would then go out and prob a bit. And then when really interesting finds came out (because of political reasons, or because of social ones) the lackeys would then turn them over to the admins of Anonymous in order to fully exploit the lead.
But that brings us back to the hacking in the news of late about the nude photos of celebrities. The nudity is salacious, and so it gets the clicks, and therefore it gets noticed. But more importantly, let’s talk about every day hacking. Right now, the single thing keeping you the most safe is your own obscurity (Security through Obscurity). The fact that no one knows or cares about you. (No offense.) Seriously though. Think about this for a moment. At the most recent DEFCON conference it was pointed out that everyone staying at the hotel but not attending the conference were called sheep. The sheep were also considered immediate collateral damage. It is well known, that if you attend DEFCON and you do not turn on off your cellphone you are meat. You are meat if you don’t turn on your laptop without active security measures. And if you do turn on your cellphone, it will probably take minutes before someone has gained access and posted your name and details to the WALL OF SHEEP board whether you are an attendee or just more collateral damage.
Think these guys are rarified wizards on the hill? That they are the exception? Think again. It make take a genius to create a new Zero Day attack vector (an unpublished weakness in an OS (microsoft say, or Linux), Content Management Solution.) but it only takes a 12 year old to click a button to exploit a zero day once its been spread through the community. And that is the other thing that happens on IRC. They discuss pontificate on all the new weaknesses bouncing around the interwebs. They get it that knowledge is power. And so they build databases and lists of weaknesses that will become useful to them one day. But this is how the world of hacking has existed for years and years. Since I knew about BBS’s, MUDs and online communities there has always been someone hacking into them.